Kali Social Media Tools is a workflow optimization and content management software designed for small to medium-sized businesses. It allows users to manage their social media marketing, create and schedule optimized social media posts, and make sense of performance analytics by generating detailed reports.
Table of Contents
Kali Social Media Tools
Kali Linux social engineering tool: Maltego
Maltego is an OSINT (open-source intelligence) investigation tool that shows how different pieces of information are interlinked. With Maltego, you can find relationships between people and various information assets, including email addresses, social profiles, screen names and other pieces of information that link a person to a service or organization.
Having all of this information can help you simulate a social engineering attack to help you evaluate your employees’ security awareness. You can launch Maltego from the Kali Whisker Menu or by going to Applications > Kali Linux > Top 10 Security Tools > and selecting Maltego at number five.
Maltego uses a graphic user interface, making it easy to visualize relationships.
Kali Linux social engineering tool: Social Engineering Toolkit (SET)
Social Engineering Toolkit (or SET) is an open-source, Python-driven toolkit aimed at penetration testing around social engineering. SET has various custom attack vectors that enable you to set up a believable attack in no time.
SET includes a website tool that converts your Kali box into a web server with a range of exploits that can compromise most browsers. The idea is to send your target a link that routes them through your site, which automatically downloads and executes the exploit on their system.
You can even use the pre-built templates in SET to clone a legitimate website so that the exploit looks more realistic. SET has pre-formatted phishing pages of popular sites, including Facebook, Twitter, Google and Yahoo.
You can open SET in Kali Linux by going to Applications > KaliLinux > Exploitation Tools > Social Engineering Toolkit | toolkit or by entering setoolkit as a shell prompt.
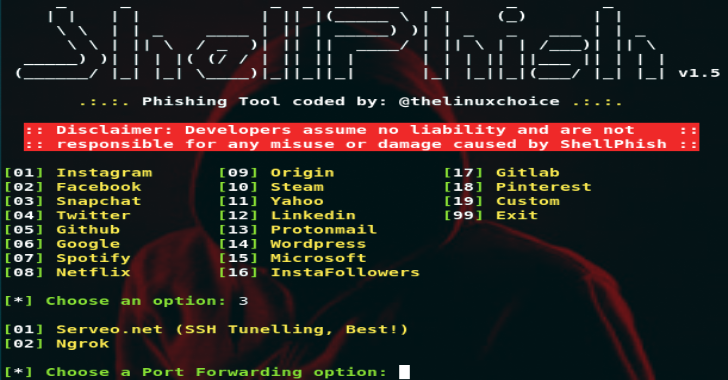
Kali Linux social engineering tool: Wifiphisher
Wifiphisher is a unique social engineering tool that automates phishing attacks on Wi-Fi networks to get the WPA/WPA2 passwords of a target user base. The tool can choose any nearby Wi-Fi access point, jam it (de-authenticate all users) and create a clone access point that doesn’t require a password to join.
Any person who connects to the evil twin-like open network is presented with a seemingly legitimate phishing page asking for the Wi-Fi password to download a firmware update, which is cited as the reason the Wi-Fi isn’t working.
Once the targets enter a password, Wifiphisher sends an alert while stalling for time. After transmitting the captured password, it will display both a fake reboot timer and a fake update screen to buy you time for testing the captured password. It’s a handy tool for evaluating your security defenses against Wi-Fi-based social engineering.
You can launch the python script by entering this command:
$ sudo python wifiphisher.py
Kali Linux social engineering tool: Metasploit MSF
Metasploit Framework is a penetration testing tool that can help you identify, exploit and validate vulnerabilities. It delivers the content, tools and infrastructure to conduct extensive security auditing along with penetration testing.
One of the most powerful features packaged into Metasploit is the option to set up a fake SMB server. This implies that when a person on the network tries to access the server, their system will have to show their credentials in terms of their “domain password hash.”
If you are patient, you may be able to capture domain credentials as users attempt to authenticate against the SMB server. Sending an embedded UNC path to the target can help you collect their domain credentials when they click on it.
MSF is updated frequently, and new exploits are updated as soon as their creators publish them. You can launch Metasploit through the Kali Linux menu or by entering the following command in the terminal.
$ msfconsole -h
Kali Linux social engineering tool: MSFvenom Payload Creator (MSFPC)
MSFPC is a user-friendly tool that makes it easy to create basic payloads. It helps users avoid the need to write long msfvenom commands to generate payloads. With this generator, you can create payloads with a minimum of one argument.
MSFPC can be used to create Windows, Linux and even Android payloads. Its script is a real timesaver when you want to create simple payloads quickly. Although this doesn’t involve encoding to help bypass antivirus virus, it can still be useful to learn.
Sometimes, you just want to make a quick payload, deliver it somewhere, and carry on with your routine. In scenarios like these, msfpc.sh can come in handy.
To use MSFPC, you must only define the payload you want by either the file extension you want it to have or the platform you are going to drop it on. Typing msfpc in the terminal will allow you to run the tool.
Utilize Kali Linux tools for social engineering defense
As you can see, Kali Linux is stocked with tools that can help you conduct social engineering penetration testing. With the help of these offerings, you can evaluate your firm’s security posture and arm personnel with the knowledge they need to avoid these threats. It’s time to close security gaps and improve your defenses against social engineering.
social engineering toolkit
In the cybersecurity world, there are many types of attacks and network threats. And among the most popular are social engineering attacks.
Regardless of whether you’re a single individual working on your own, or an employee from a mid- or large-sized company, you can be never safe from social engineering attacks. It’s one of the most popular types of methodologies used by crackers to capture your sensitive data.
When a social engineering attack is performed, the weakest link in the chain is not the computer system, the firewall, services or apps. It’s us, the humans behind those technologies.
Fortunately, social engineering techniques and attacks aren’t only used by bad guys, but also by blue teams as a way to educate employees and general staff about avoiding these malicious traps.
That’s why today we’re going to review one of the most popular social engineering tools around: The Social Engineering Toolkit.
What is the Social Engineering Toolkit? (SET)
Known as SET, the Social Engineering Toolkit has been in wide use since its creation.
Written by Dave Kennedy from TrustedSec, it’s an open source, free Python cybersecurity tool used by security researchers, penetration testers, blue and purple teams from around the world. Instead of targeting apps, SET uses humans as the main target of its attack techniques.
It offers many brilliant features, including faking phone numbers, sending SMS, or helping to create a phishing page by instantly cloning the original. Let’s explore the full powers of this toolkit:
Main features:
- Multi-platform: It can run on Linux, Unix and Windows.
- Supports integration with third party modules.
- Allows multiple tweaks from the configuration menu.
- Includes access to the Fast-Track Penetration Testing platform
- Social engineering attack options such as Spear-Phishing Attacks, Website Attacks, Infection Media Generator, Mass Mailing, Arduino-Based Attack, QRCode Attacks, Powershell Attack Vectors, and much more.
SET offers multiple attack vectors and techniques, and it’s almost impossible to cover them all in one article. However, we can highlight the main attacks here:
Phishing Attacks: This option allows you to choose from several phishing attack options to help you decide how to approach your victim. You can craft email messages with malicious payloads attached, and send them to a small or large number of recipients.
It also lets you spoof your email address by changing simple variables, which makes it really easy to use.
Web Attack: This module combines different options for attacking your victim to compromise the remote victim. It includes attack techniques such as Java Applet Attack and Metasploit Browser Exploit to deliver malicious payloads. Also handy is the Credential Harvester method, which lets you clone a website and harvest the information from user and password fields, as well as the TabNabbing, HTA Attack, Web-Jacking and Multi-Attack techniques, all with the same goal of tricking end users into revealing their credentials.
Infectious Media Generator: This interesting option enables you to create an infected media device (USB/CD/DVD) with an autorun.inf file, that can be later inserted into any PC and will automatically run a Metasploit payload if autorun is enabled.
Create a Payload and Listener: By using the fourth option from the main menu, you’ll be able to create malicious payloads for Windows, including Shell Reverse_TCP, Reverse_TCP Meterpreter, Shell Reverse_TCP X64 and Meterpreter Reverse HTTPS. As you can see by the names, you’ll be able to spawn command shells, create reverse connections, tunnels, and more.
Mass Mailer Attack: This type of attack can be performed against one or multiple individuals, even letting you import users lists to send to any people you wish. It also lets you use a Gmail account for your email attack, or use your own server or open relay for mass delivery.
Apart from these main options, you’ll also find other useful attack choices such as Arduino-Based, Wireless Access Point, QR Code Generator and Powershell Attack Vectors.
Now that you have a general overview of the Social Engineering Toolkit, let’s jump into the fun part, installing and testing this software.
Installation
Installing the Social Engineering Toolkit is pretty easy with most operating systems. On most Linux distros the manual installation can be performed by using the following commands:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
cd set
pip install -r requirements.txtJust make sure you have pip installed.
How can I use it?
Once you have SET installed, you can easily invoke it from command line by typing:
./setoolkitFirst you’ll see an agreement message. Read it, accept it and that’s it, you’re ready to use this tool. Then you’ll probably see the following welcome message: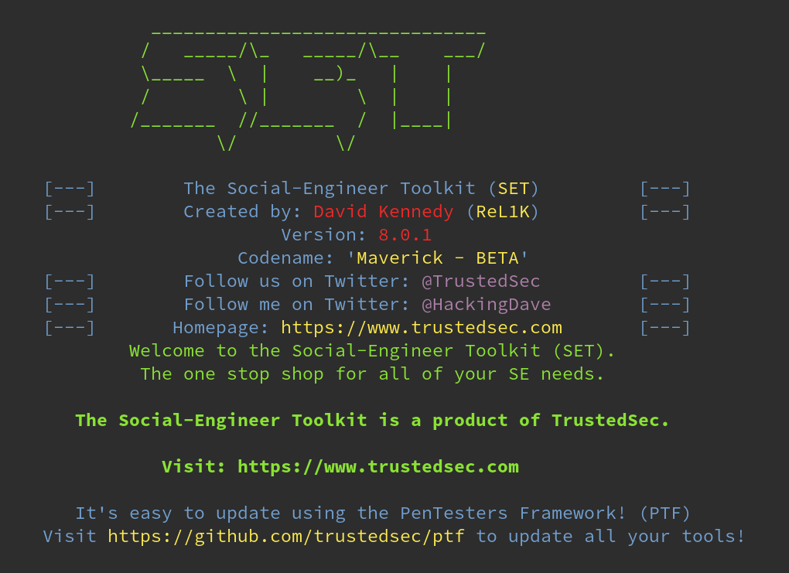
After that, you’ll notice a menu, showing you the most common options: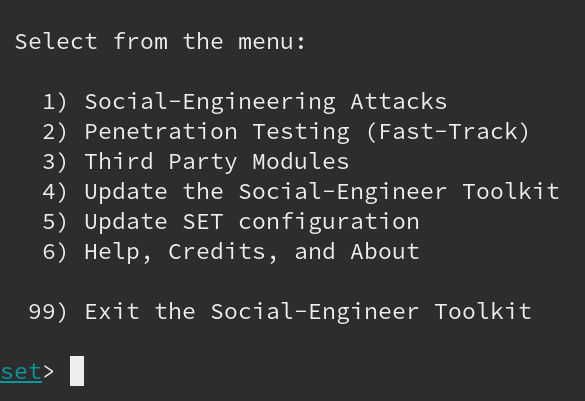
If you click one of them, you’ll get the full list of available attacks. For example, we chose number 1 and this was the full available menu for that option: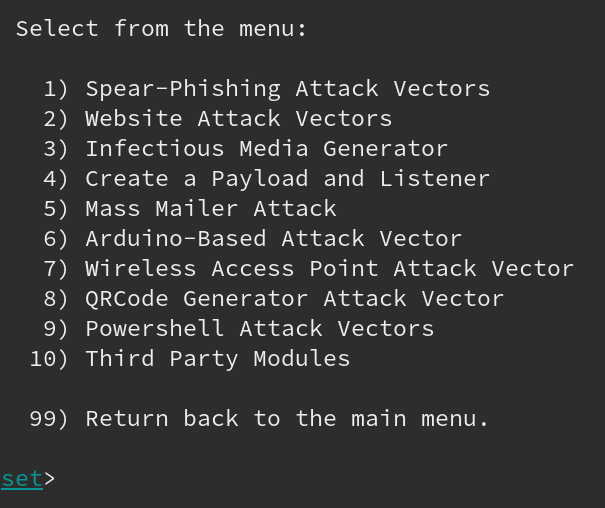
The same goes for the rest of the options offered. Simply choose the type of attack you wish to perform, then configure the way to perform it.
When talking about social engineering, one of the most common methods that comes to mind is the use of phishing emails. Let’s see how good SET is in this particular area.
We went back to the main menu, chose option 5, and this was what we got: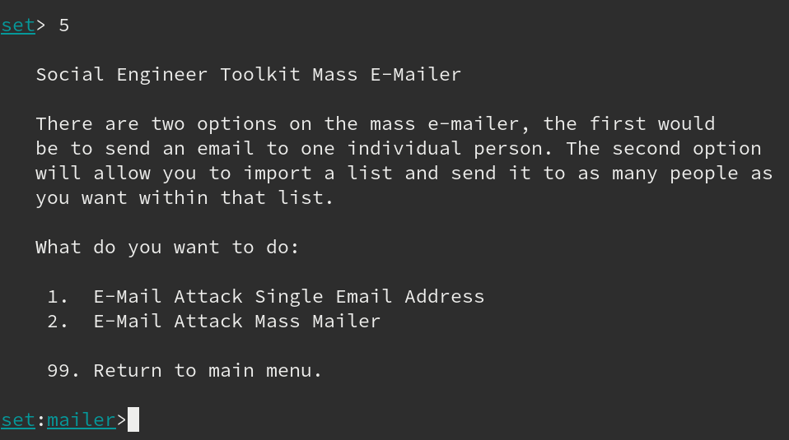
As you can see, it lets you choose from two different options: either email a single address, or multiple ones. We’ll go for the single email address. Once we’ve chosen that, it shows us the following screen, where we can actually start the phishing email attack: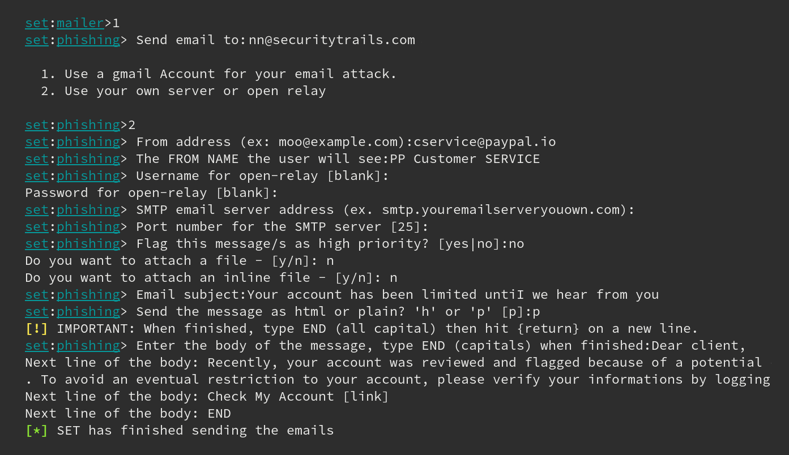
We used a phishing email example, taken from a real-world Paypal phishing attack, to see it live in our email test box. Of course, a bit of formatting was missing from our example, but it was just that, a live test playing with this tool. A real attacker would put greater effort into both email style and text, of course.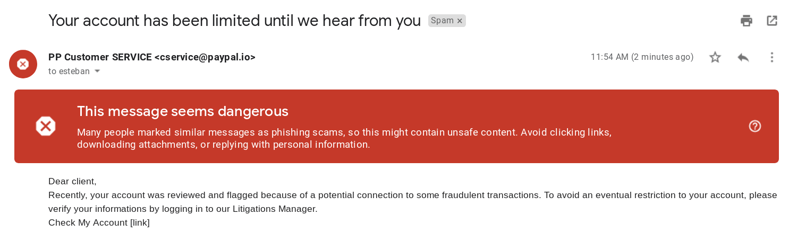
As you can see, the email arrived perfectly—but thanks to the Gmail filter, it was flagged as spam and potentially ‘dangerous’, as well as labeled as ‘phishing scam’.
Conclusion
Let us know your thoughts in the comment section below.
Check out other publications to gain access to more digital resources if you are just starting out with Flux Resource.
Also contact us today to optimize your business(s)/Brand(s) for Search Engines
